I’ve exhausted my WaPo views for the month and am too lazy to jettison my cookies to hop over the firewall, but according to MSNBC, Bart “Not-Greenwald” Gellman and Ashkan “Not-Poitras” Soltani published an NSA bombshell today:
The Washington Post reported Wednesday that the NSA hacked into the data centers of Yahoo and Google – two of the biggest email and cloud storage providers. It cites documents leaked by former NSA contractor Edward Snowden.
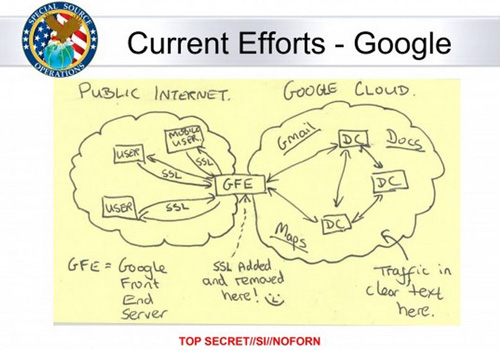
According to WaPo, the hacking was accomplished using an NSA tool called MUSCULAR. If you think that’s a stupid name, wait until you see the “Google Cloud Exploitation” slide that describes it from the NSA presentation, which I managed to snatch off the WaPo site before they gave me the bum’s rush:
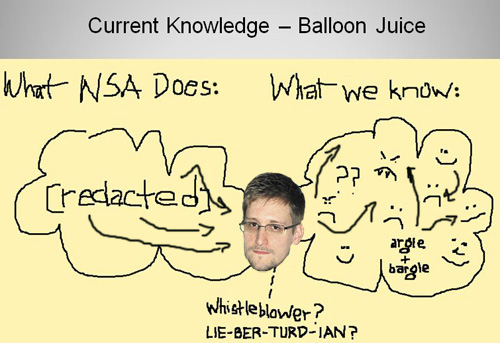
Sweet cartwheeling Jesus. While we technologically inept folks await a verdict on whether this latest “bombshell” is a nothingburger or somethingsalad, can we just pause a moment and reflect on the implications of this toddler-level depiction of the possibly monstrous privacy destructorator? Here’s an illustration of our collective pause, which was created in PowerPoint and Paint in three minutes flat by my dumbest chicken:
I’ll back her up against the NSA graphic design team any fucking day.
Now, on to weightier matters. It has been suggested in alternate quarters that your Balloon Juice team is a frivolous, feckless flock of fooking trolls, authoritarianism aficionados and bitter PUMA cat ladies who are not a’tall interested in a rational discussion of the true issues surrounding surveillance and security.
This is 100% true. However, just yesterday, valued commenter Jockey Full of Malbec, who has excellent taste in wine and is therefore trustworthy, did suggest some questions that could lead to a rational discussion:
(1) What level of secrecy WOULD be acceptable to you?
(2) What checks and balances would you like to have that are NOT currently in place?
(3) What concrete legislation would you propose to achieve (1) and (2)?
(4) Which elections in 2014 and 2016 should sympathetic Democrats target to achieve (3)?
And equally valued commenter Omnes Omnibus elaborated upon JFOM’s suggestions in that same thread with the following:
I would suggest adding: “How much surveillance is acceptable?”, “What types? Metadata, e-mail content, phone locations, phone conversations, CCTV?”, and “What should be the standard for allowing the surveillance? Probable cause, reasonable suspicion, etc.?”
Moreover, your humble correspondent brought up proposed legislation that was once entertained in the US Congress and begged for your insights just a few days ago, albeit in the middle of an NSA thread that reached .5 TBogg proportions, which is akin to farting in a whirlwind (i.e., not very ladylike). Anyhoo, here’s that:
So the question becomes, what are the proper limits? What constitutes adequate control? Here are some proposals entertained in Congress:
Restrict or end bulk records collection and limit surveillance to individuals who merit surveillance due to probable cause
Require government analysts to get court approval before accessing incidentally collected data from Americans
Require executive branch reports to Congress on how many American communications are swept up during surveillance
Require the DOJ to produce a public report giving aggregate data on how many people have been targeted for surveillance
Restrict the use of gag orders related to surveillance court orders (see FISA Court motions by Google and Microsoft)
Declassify significant surveillance court opinions, with redactions as necessary, of course
What do you think? Are these sensible? Too restrictive of government surveillance powers? Do they not go far enough?
What say you?
Southern Beale
So glad I’m not on the cloud.
taylormattd
So is that slide the evidence of the nefarious program? Or is there more?
Southern Beale
BTW I’m about half-way through Dave Eggers’ The Circle and 1/3 of the way through Margaret Atwood’s MaddAdam. I’m kinda in a post-apocalyptic death spiral as a result, but there’s a lot of overlap between these two novels and the issues of privacy, social media, technology, etc.
Trying to wrap my head around the idea in Eggers’ book that “privacy is stealing” and “sharing is caring.” LOLZ
Corner Stone
PUMA Cat Lady!
Belafon
I like the smiley face.
Corner Stone
BTW, I love the way your dumbest chicken is really dense but even she knows enough to put fangs on the angry face depicting commentor Botsplainer in the right side circle.
Ripley
Stop Drawing Us.
gussie
I guess I don’t really understand the NSA’s mission. They’re trying to capture all the digital data in the world, so if anyone commits a crime, they can figure out who it was, and who the accomplices were? And if anyone’s planning a crime, likewise? That’s the goal?
David Koch
I knew this was gonna happen once Dictator Obama hired Michael Westen.
Corner Stone
Of course, all the BJ Sophisticates will clearly elucidate for you that this is, indeed, a Yawn. Known. Burger.
But I find it at least potentially amusing that Senator DiFi, long a supporter of things known to intel briefed elected senators, has claimed that even *she* did not know the breadth of what the NSA is up to.
And yet, somehow, all of our natsec experts here did, indeed, know more than Senator DiFi.
So, I can only conclude that we’re good here.
Comrade Scrutinizer
@Southern Beale: I liked Suarez’ Daemon and Freedom (TM) for that.
scav
Apparently my cunning plan of writing all my secret plans on yellow stickies and affixing them backwards on Mr ipad iscreen isn’t so cunning after all. isigh.
schrodinger's cat
Since it is appropriate, NSA kitteh, is watching you.
Corner Stone
@gussie: It’s even better than that. They saw the TV show “Person of Interest” and got totes jelly.
They don’t just want all the data. They want all the potential data so they can pre-cog the hell out of some shit.
Violet
Are you asking people to have a serious conversation about this topic? What’s wrong with poutrage, grandstanding and indignation?
Yatsuno
MY NOSE DOESN’T LOOK LIKE THAT!!!
Ms. D. Ranged in AZ
Well, crap, this is a somethingsalad from an IT perspective. It’s not news that all data is vulnerable in transmission, even when encrypted. But the fact that they hacked a Google front end server and purposely put SSL code on it without permission to gather data is bad, bad, bad.
I’ve spent a lot of time going off on Snowden and Greenwald for the nothingburgers so far. But this, at first blush, appears to be something that should get everyone’s attention and anger. Maybe now the press will stop trying to put Sibelius on a stake for public execution. Whee! Isn’t this all so much fun.
BGinCHI
I want all the benefits of privacy for myself but none for anyone who breaks the law or wants to harm Americans, no matter what the historical or political context.
/snapshot of USA, 2013
JustRuss
Gag orders. In a Free and Open Society(don’t laugh!), I can’t see a case for them except in extreme circumstances. There’s no excuse for them to be SOP.
schrodinger's cat
Am I the only one who hates the recent changes to Gmail? I hate the Gmail is trying to become too Facebooky. Any other alternatives out there?
Southern Beale
@schrodinger’s cat:
Yahoo email has done the same thing. I just use Yahoo as my backup email account to avoid Spam but it’s become nearly impossible to use because of the gadgets and gewgaws.
Also: I DO NOT WANT TO CHAT WITH ANYONE. EVER.
Leave me the fuck alone. I don’t get the chat part of Yahoo.
BGinCHI
@schrodinger’s cat: Apparently you can just write on paper and send it to people. I have no idea how that can work but I bet you don’t even have to have friends to use it.
catclub
@Southern Beale: I think Dilbert had it right.
They do all their backup via NSA.
schrodinger's cat
@BGinCHI: Seriously, live without email? You can’t be serious.
David Koch
BGinCHI
@schrodinger’s cat: Just think how cool this blog would be if after each post we had to mail in our responses, then Cole would post them and we would mail in replies.
This could free us up to get other things done. Though Cole would be fucking swamped. Though less lonely.
Violet
@Southern Beale: Yahoo mail is awful now. It kind of doesn’t work like email. I can’t even get something simple like the font size right. It’s either so tiny I can’t read it or giant like large print. That’s the leap from medium to large, so its not like there are other good options. It’s ridiculously hard to use.
schrodinger's cat
@BGinCHI: Steve will sit on our mail, my kittehs love doing that, sitting on papers especially the stuff I am working on.
Elizabelle
Betty: am sure you got the gist of the WaPost story, but I emailed its contents to you.
tommy dee
@Southern Beale: just to be clear, the epigrams in ‘The Circle’are not favored by Eggers’. He’s strenuously against them.
ranchandsyrup
I only wanna be “kept safe” when there’s a republican president. Or even Rand Paul.
BGinCHI
@Violet: I agree completely. I use it but it sucks royal. Yahoo Groups is now totally unusable. It’s like trying to pilot a Soviet spaceship.
The font thing is especially annoying! WTF!
Does anyone use Apple’s native mail thing?
BGinCHI
@ranchandsyrup: How’s the baby? Sleeping?
srv
The really interesting thing here is that Teh Google didn’t decide to encrypt within their cloud until after the Snowman files.
So, the agency had to tell their Prism partners that they were going to be exposed and Larry and Sergei needed a story to fix the back door… which implies they knew about the back door…
Howard Beale IV
@Southern Beale: Just think-sometime soon retrocomputing may be the answer to protecting one’s self-after all, how many OS/2 hacks are there out there for exploitation?
ranchandsyrup
@BGinCHI: she’s doing pretty well. Up a couple of times a night. big sister and I are quarantined due to flu-like symptoms. :(
Things well with you and yours?
Roger Moore
@gussie:
Their mission is actually twofold:
1) Carry out electronic espionage against other countries
2) Help to protect America from foreign electronic espionage
It seems to me that there are three basic categories of problems I’ve seen people talking about in relation to this:
1) Is the NSA spying (or even inadvertently collecting data) on Americans, which is outside its job and (without a warrant) against the 4th Amendment
2) Is the NSA spying on friendly countries
3) Is the NSA undermining cryptographic standards to make job 1 easier and thus undermining job 2.
Of these, 1) is clearly a legitimate point that requires a lot of discussion. Point 2) is arguable. There’s good reason to look at friendly countries, but we need to be very careful in doing so not to piss them off. Point 3) doesn’t seem to have gotten much discussion outside of fairly hard-core crpyto circles, but it’s potentially a big worry. Good cryptography is important for all kinds of real business, and secretly sabotaging it puts us all at greater risk of having various bad guys steal our data.
Corner Stone
@BGinCHI:
Wait…how would *you* know?
COMMIE PINKO SCUM!!
BGinCHI
@ranchandsyrup: Taking antibiotics for the first time in 20+ years for a sinus/chest thing. Getting it from the boy’s exposure at half-day daycare (“half the day…all the germs, guaranteed”). Will mend soon though I’m sure.
I bet she’ll sleep soon, once she gets settled. Feel better man. No tricks or treats for you.
BGinCHI
@Corner Stone: I live in a junkyard. Like Ralph in Wreck-It Ralph, but with smaller hands.
ranchandsyrup
@BGinCHI:
Outstanding! Needed that laugh. Thx.
jayackroyd
Well this is of course tendentiousness rather than constructive, but:
(1) What level of secrecy WOULD be acceptable to you?
Operational secrecy on actual military maneuvers or planing
(2) What checks and balances would you like to have that are NOT currently in place?
Enforcement of existing law would be a good place to start. Then I’d dismantle the NSA and CIA and start from scratch. We don’t have an enemy threat that justifies the existence of these institutions as currently formulated. And they suck at their jobs.
(3) What concrete legislation would you propose to achieve (1) and (2)?
Now you’re just being silly. Current legislation is not being enforced. The issue is that the administrations are breaking laws and neither Congress nor the courts are acting.
(4) Which elections in 2014 and 2016 should sympathetic Democrats target to achieve (3)?
primary Feinstein.
The Sheriff's A Ni-
Thirty-six posts and I don’t see anyone answering our humble correspondent. I think that says a lot about everything, really.
That said, I think your suggestions might be a little too restrictive but its a good place to start. One would want a balance between ensuring potential targets aren’t spooked into the next flight to Kabul, all the while ensuring that any data collected won’t be used against innocent civilians. I imagine its a delicate balance.
LanceThruster
“We demand rigidly defined areas of doubt and uncertainty!”
kindness
Hacked? The AT&T switching center in San Francisco has a room right off of it that no one can go into unless they have NSA credentials. It is reputed to vacuum up every e-mail, fax & phone call that goes through it and it is the hub for traffic going overseas.
Me, I believe Yahoo & Google gave them the keys just like At&T did.
Howard Beale IV
@The Sheriff’s A Ni-: If the NSA has successfully broken SSL and created a reliable, near non-traceable MITM attack, then kiss internet banking and everything else goodbye.
You’ve just turned the internet into CB radio and destroyed banking and commerce-who the fuck would be willing to trust compromised infrastructure?
The Sheriff's A Ni-
And no sooner do I do so than Roger comes out with a good post and Jay breaks out the Flower Power signs and Grateful Dead reel-to-reel bootlegs. I stand corrected.
jayackroyd
@Roger Moore: They aren’t cracking encryption. They’re circumventing it, or doing traffic analysis (tracking metadata) Or doing things like encouraging my cable company to cripple my password, making the first 10 characters of the 16 char password to be the same as my SSID, and not allowing me to change it.
BGinCHI
@The Sheriff’s A Ni-: I’ll give you my honest answer.
It’s a gigantic fucking waste of money. Democracy is risky. Let’s build a smarter and more caring nation instead of a bunker full of idiots, plutocrats, and militarists.
We are the aged paranoid king who has no friends and can trust no one. Gosh, there must be a story about this somewhere.
Omnes Omnibus
The NSA hacking Google and friends thing sounds ugly at first glance. I have, however, started making an effort to withhold judgment on breaking news. I’d like to at least be able to pretend to myself that I know what I am talking about.
On the broader surveillance and security issues, I tend to oppose anything within the US that is not specifically targeted. Basically, I think that if you want to wiretap someone, read someone’s email, etc., you should be able to explain why you need to do it in a way that satisfies a judge. Outside the US, I would have far looser criteria. I don’t see any reason that we should be trying to scoop up the communications of every Gunther and Pierre in Europe, but I think it benefits us as a country to know as much as possible about what is happening in the world. Merkel’s cell phone was a stupid move. Anything significant she would say over a phone would not be said on a cell, so the potential reward is pretty small. We are see what the risks are. Not worth it.
mclaren
(1) What level of secrecy WOULD be acceptable to you?
Everyone should be forced to film themselves shitting and fucking and broadcast the results on giant screen OMNIMAX theaters throughout the nation.
(2) What checks and balances would you like to have that are NOT currently in place?
The death penalty for using cellphones, smartphones, tweeting anything, or using the word “cloud.”
(3) What concrete legislation would you propose to achieve (1) and (2)?
Random beatings administered to twenty-somethings who work in Silicon Valley until their main innovations consist of “new types of potholders” and “useful drink coasters.”
(4) Which elections in 2014 and 2016 should sympathetic Democrats target to achieve (3)?
Obviously, the presidential election. Also a new position should be created called Central Scrutinizer consisting of a person who is required to watch newly-posted YouTube videos of dogs on skateboards and waterskiing squirrels 70 hours a week and deliver a daily report to the president in the form of a Skateboarding Dog Matrix, listing the types of dogs currently threatening to skateboard, and the locations where these events might occur. JSOC assassination squads can then be dispatched to these locations to neutralize the threat of skateboarding dogs before it occurs.
Lyrebird
You guys are awesome, and so is she:
http://www.rawstory.com/rs/2013/10/30/12-year-old-suffragette-fires-back-at-nc-gov-for-voter-suppression-i-am-not-a-prop/
(O/T)
mclaren
@jayackroyd:
Yes, to clarify this, any system that uses encryption must at some point decrypt the information in order to use it. The NSA appears to have inserted backdoors into computer systems after the encrypted info gets decrypted. At that point, it’s plaintext, and anyone can read it.
The logical end result of this kind of snooping is that sometime in the near future you will be summoned into the office of your local police department to explain to a group of officers:
1) Why you found it necessary to wank off to the movie NINJA NUNS IN BONDAGE 3: THE RETURN OF THE JUMBO-SIZE SPATULA;
2) How many times you wanked, what form of lubrication you used, and which locations in your house or apartment you occupied during said activities;
3) The estimated volume of fluids produced during said process along with a timestamp on the video showing the duration of these activities.
This will be followed by a multiple-choice questionnaire about the putative awesomeness of Raquel Welch wearing a blonde wig and shouting caveman talk in the 1966 film ONE MILLION YEARS B.C. Criticism of the appearance of dionsaurs along with humans, which is not scientifically accurate, may improve your cumulative grade.
J R in WV
I think that if they want to look at everything we the general public do and say, that’s fine. IF we get to see everything they (the rulers of the universe in Congress and the Executive Branch AND the Judicial branches of government) do and say.
If they want to hear us peoples say “OH Baby, that’s so Good, do it harder!” and see us via our web cams on our laptops, fine. I just want to see them fucking that chicken! You know, harder and harder and deeper into that chicken.
Or Duck. I think Geese are too big and mean to play with, but whatever. And if they’re getting it with hoes, that should be on TV!
Otherwise they need a warrant based upon real evidence of probable cause presented to a Judge, who should be aware that all his privates will be on cable TV the next day.
What do you think, fellow BJers, would this prevent most evesdropping or what? It isn’t my idea… it was in a FICTION I read once a long time ago. If everything is public, then nothing is private.
jayackroyd
@mclaren:
An alternative approach is that all elected officials’ travel, telecom and purchasing activity should be posted on web databases. .
BGinCHI
@mclaren: Raquel Welch on roller skates? Hubba.
Howard Beale IV
@BGinCHI: Gaaah: I hate to outsource to Sully, but so be it.
jayackroyd
@mclaren: yeah. that smiley face isn’t a super factoring device that they’ve worked out in the bowels of ft meade. Although I echo atrios. why are they doing this? It’s a huge waste of money.
mclaren
@J R in WV:
PAUL RYAN: “That chicken is free to maximize its earning potential by participating in this process. That’s the essence of the free market. As Dagny Taggart said in her immortal speech in the book “Atlas Shrugged,” `Every dollar we spend is not ours, but a lien on the genius and creative potential of every chicken that allows itself to be fucked.'”
JOHN SCALIA: “Chickens are not people and do not have fourteenth amendment rights. Therefore the supreme court should refuse cert on any cases involved chickens and people, especially cases involving chickens and senators. Or chickens and presidents from Texas.”
ANN COULTER: “This is so typical of the Democrats, who have been hateful chicken-fuckers since day one. I’ve never seen a Democratic chicken who wasn’t eager to get fucked, especially when it was a Republican senator doing the fucking. Which never happens. But if it did happen, is what I mean. Hypothetically speaking. In a bathroom. In the Ronald Reagan national airport.”
Corner Stone
I’m kind of hoping there actually is a movie called “Ninja Nuns in Bondage 3”
If the NSA can actually provide a link to this movie then I will consider its mission statement a success.
Mnemosyne
Uh, why the hell would someone make a sketch on a Post-It note, scan it, and insert it into a presentation rather than, you know, using the presentation software to make the flowchart?
And, yes, that sketch above is not one of Betty’s joke — it’s claimed to be the real thing.
JC
I said this in the last thread, I will say it again.
NSA is going to cost Google, Facebook, Microsoft, etc, huge amounts of money, simply because they are forcing compliance for snooping and eavesdropping that – eventually – countries and people from other countries will reject.
NSA, assorted agencies, and assorted contract companies – skimming tens or hundreds of billions in contracts, that are paid for by you and me – will be ACTIVELY causing financial harm, to our best and brightest companies, as well as the jobs that will not be created.
These guys are taking OUR money to eavesdrop on us, take away our best jobs, and actively hurt the economy. Profit!!
I like the list of the reforms you mention in the post. The problem, as always, is that unaccountable power, always breeds abuse, and the rationale for more unaccountable power. Your list of reforms puts at least some breaks on this.
Gin & Tonic
@kindness: There is no such thing as “*the* hub for traffic going overseas.” There are multiple exchange points for data traffic, and multiple cables; in many cases the terminating equipment is not operationally controlled by a US-based company. Look at http://www.submarinecablemap.com to get an idea of how data packets travel around the globe. AT&T is actually a fairly small player in this market.
Gin & Tonic
@schrodinger’s cat: Free e-mail is worth every penny you pay for it.
If you want real, reliable e-mail, pay for it. Preferably with a provider whose data center(s) are based in countries that do a better job of protecting personla privacy.
mclaren
@Corner Stone:
Rule 34. “If it exists, there is porn of it.” A friend once showed me a Japanese fetish site that offered custom sex videos. One of the videos involve a woman stepping on HO-gauge model trains with with high heels in order to crush the trains. This apparently provided sexual gratifcation for some of the viewers of that site.
Mind you, there were different sections for HO-gauge and O-gauge trains. Apparently, the type of train being crushed with high heels made a crucial difference.
Omnes Omnibus
Also, BC, I think your list is a good start of fairly concrete places to start. The big hurdle is getting a political establishment that will talk to the American people like they are adults about security issues. We can’t be perfectly safe. We can just try not to miss the major shit. The vast majority of the political establishment will not say that. Some because they are too dumb to know it. Some because they benefit from infantilizing the population. Some because they are cowards. If you know that you can’t be perfectly safe no matter what, you can better determine whether you are willing to give up some more privacy for a marginal increase in safety.
Higgs Boson's Mate (Crystal Set)
@Howard Beale IV:
Did IBM ever fix the Disk 2 problem with OS/2 Warp? Me, I use BeOS. Hack that muthafuckas.
mclaren
@Omnes Omnibus:
This is not possible until the American people begin behaving like adults about security issues.
kindness
@Gin & Tonic: Screw you. When it came out during bush43 I was pissed. I still am. The fact that it’s now Google and Yahoo doesn’t inspire confidence.
Betty Cracker
@Mnemosyne: Maybe it was a contractor chicken?
Howard Beale IV
@Higgs Boson’s Mate (Crystal Set): I think they did, once they sold it off and became EcomStation.
Now I’d like to see these guys break a Burroughs Medium System virtual machine. Or a TI DX/10.
But what we really need to resurrect is Multics.
Omnes Omnibus
@mclaren: Actually, twelve years after 9/11 and five years after we got a president that doesn’t push fear of everything, I think the American people are ready for it. As a general rule, Obama has operated that way and he seems to be getting away with it.
Botsplainer
@mclaren:
You could pay for the whole structure of the Internet just by making this a pay per view subscription service for home viewers.
Gin & Tonic
>> @kindness
>> Screw you.
This is funny.
geg6
I want warrants for any American’s communications. I want an end of gag orders for FISA courts. I want, redacted if necessary, court transcripts. I can’t get too exercised about them monitoring communications for information on terrorists but I ‘d like them not to be able to store superfluous communications, the vast majority. If they can’t monitor or store pertinent info, then they should be able to get it, with a court order, from the communications companies and tech companies who collect it all anyway. I accept the need for national security, but there should be some transparency.
I don’t like it, but I accept the need for some of this, with at least a passing nod to constitutionality.
Higgs Boson's Mate (Crystal Set)
What kind of Congressional oversight of the NSA is taking place when the Chair of the Senate Select Committee on Intelligence doesn’t know that the NSA is monitoring the cell phone of a foreign head of state?
Botsplainer
@mclaren:
My Netflix queue is supposed to be visible only to me and my NSA minder. Why have you been getting access to my viewing habits?
Central Planning
That GFE piece – sure, the NSA might have hacked it. That’s not really news, is it?
The thing is people don’t really understand SSL, certificates, and how it all works. Chances are if your workplace has a proxy server, or something to “manage” who can get where, most likely they are decrypting, analyzing, and re-encrypting your data. And, they can configure your corporate machine so you don’t get the warning message.
How many people blindly click “OK” on the warnings of “this site may not be what you think it is?”
And if you’re in to wireless hacking, I learned about this beauty last week. For $99, I’m thinking about getting one to show to customers.
Omnes Omnibus
@Higgs Boson’s Mate (Crystal Set): I don’t really believe DiFi’s denials.
geg6
@Omnes Omnibus:
Yeah, me neither. Damn, if there’s a Dem that needs to GTFO, it’s DiFi. I would think that’s a safe seat out there at this point.
Central Planning
Oh, and one other reason you would decrypt everything that you (think you) know stays inside your network: you can then control that data – prioritize, traffic-shape, rate-limit, block, etc.
Howard Beale IV
@geg6: Agreed. DiFi need to retire and never utter another word.
Howard Beale IV
A New Hope has just surfaced.
jayackroyd
@Corner Stone: Sadly, when you google NNiB3 you get this thread.
Omnes Omnibus
@jayackroyd: So “skull fuck a kitten” and NNiB3 will be this blog’s legacy. I suppose that means something.
e.a.f.
Can’t figure out why they are doing all this snooping except it makes a lot of money for the companies doing it. Capitalism at its best. None of it should be on. No snooping, no spying. All of this simply confirms we don’t have any freedom. All we get to do is decide which party spys on us.
All the spying may assist “authorities” in arresting people after an “incident” but not prior. If the government’s excuse is, they are preventing terroism, they have failed. The real terror these days is sending your kid to school and finding out they have been shot to death. The real terror is you are driving down the street and get hit by a drunk driver. The real terror is a drug house opens next door to you. The real terror are the drive by shootings, family violence, homeslessness and poverty. Has any of this survellence helped? Not one bit. It hasn’t even reduced crime in the U.S.A. Why? Well because they can’t take the information to court in a criminal case. So if you can’t use it against a criminal, then you shouldn’t be able to gather it on the rest of the world. Spying on the Chancellor of Germany? the Americans are truly stupid. Some one is making a great deal of money on all this spying. If they stopped to morrow morning, the government could save a whole lot of money.
Jennifer
What say I?
I say that your dumbest chicken missed a real opportunity with the two bottom arrows in cloud on the left, which she could have easily turned into a dick.
bemused senior
@Howard Beale IV: The cartoon doesn’t imply that ssl was broken. It implies that the Google and Yahoo production intranet was broken into. Customer uses of SSL terminate at the gateway into that intranet. Someone on the inside has access to lots of unencrypted data. That doesn’t mean that they have access to all the data, but the WaPo article says that the private fiber linking the data centers that are the internal production network in each case was snooped. Now, I know about one of these orgs, and many data flows that cross data center boundaries are encrypted, but not all, and many older apps or apps with ginormous (technical term) magnitude of data are not encrypted. So those flows are subject to inspection by someone able to tap the inter data center private fiber.
different-church-lady
@Southern Beale:
After two weeks of trying to get used to it, I stumbled across some sort of switch that took me back to a “classic” or simplified interface, and since then everything’s be a lot easier (even though some actions require more clicks).
Pogonip
@BGinCHI: I was just reading a discussion of e-books on another site. One commenter said his kids didn’t know how to write a check or address an envelope. If we use paper, we can bring the surveillance state to its electronic knees! Be’s-ha-ha-ha!
different-church-lady
Look, I’m tired, I’m suffering writer’s block on an important job cover letter, and the Sox are about to win another World Series. Can’t we just invoke the 24 hour rule and talk about this tomorrow? Because it looks like we could actually have a sane conversation about it, but I’m going to have to take a pass tonight, and that’s a drag.
Just Some Fuckhead, Thought Leader
I believe the actual phrase is “nannies, grannies and trannies”.
different-church-lady
@mclaren: You’re capable of sarcasm. I hadn’t thought it possible.
jayackroyd
@e.a.f.: Actually I’ll be talking to a security professional about precog tomorrow night. You do realize that the US drone strikes are preemptive, not retaliatory. They identify likely terrorists and take them out. This kind of massive data collection on individual activity could easily turn into projected activity. And, of course,they’d work out the details of precog in secret promising us, as in the Minority Report, that the methods are infallible.
different-church-lady
@BGinCHI:
I just switched to a 4 year old version of it (which is the most recent version that will run on this 5 year old computer) Not bad, but has some definite disadvantages to what I had been using (a MUCH older version of Eudora, which could do things that Mail can’t do, but was also starting to crash twice a day).
Just Some Fuckhead, Thought Leader
@different-church-lady:
NSA gotcher tongue??
Figures.
different-church-lady
STRIKE ONE! WE’VE GOT IT LOCKED UP!
different-church-lady
@Just Some Fuckhead, Thought Leader: You think if I pick up my phone and plead my case, the NSA might send me some example cover letters I could just search-and-replace with my own info?
Omnes Omnibus
@different-church-lady: Typing that comment might have been enough.
different-church-lady
@Omnes Omnibus: You know, I could use a pizza too…
Just Some Fuckhead, Thought Leader
@e.a.f.:
Maybe, but you know the libertarians are the only ones masturbating to it. If spying has to happen, it should at least not be icky.
Betty Cracker
@different-church-lady: Believe it or not, I excel at cover letters. And I would be happy to assist. You can click my author link above for my Gmail — just give me a heads up here if you do. I don’t get around to checking it all that often..,
Omnes Omnibus
@Betty Cracker: Thanks for putting up this post.
different-church-lady
@Betty Cracker: I deeply appreciate the offer, but I have an extremely strict thing about not ever revealing any information about myself whatsoever to people I know only on the internets.
However, if you’re willing to throw me a bit of advice right here, this is what I’m struggling with (besides my usually glacial writing pace…)
There’s a job I’m extremely qualified for from the aptitude and and related experience angles. However, (a) none of my experience is direct and (b) I have such an eclectic jumble of work experience from my freelancing that it’s hard to create a coherent mini-narrative that doesn’t sound like a hodge-podge.
I might be a little too hung up on the advice that one should cite “specific examples” — all my specific examples would make the experience seem tangential. (I wouldn’t have this problem in an interview, because I’d be able to guide the back and forth away from how things were dissimilar to how they related without the constrains of being concise in extreme.)
GHayduke (formerly lojasmo)
Ahhhh! The NSA is hacking my, um…playlists.
Okay.
Mnemosyne
@different-church-lady:
As I understand it, a big problem with cover letters (and resumes) right now is that humans don’t read them — you need to figure out which keywords the employer is looking for and make sure you include them. Otherwise, your letter won’t “pop” when they scan it in and will never be looked at by an actual person.
Weirdly, knowing which keywords they want might actually make it easier for you to compile everything semi-coherently.
Just Some Fuckhead, Thought Leader
@different-church-lady:
I read cover letters every day. You aren’t going to be able to overcome the resume with a cover letter. You’d do best not to even mention your credentials. Rather, you want to show warmth, enthusiasm and spontaneity in the cover letter and, most importantly, a familiarity with the company. When I read a cover letter, all I want to know is “do I want to meet this person?”
ETA: Well, yeah, assuming a human reads it.
fuckwit
First of all, SSL is over. It’s not secure. That little “lock” icon you see? It means fuck-all. NSA and even ISP’s can present certificates that your stupid browsers will stupidly accept, and thus all your “encrypted” traffic is unencrypted and sniffed by whomever the fuck wants to: your ISP, the NSA, anyone. It’s called a “man in the middle attack”, it’s a common security threat, and NSA is confirming they are executing that. I’m not surprised. But I’m upset too. This does need to get more firmly regulated.
Secondly, I knew the cloud backlash was coming. And here it is, not a minute too soon.
I have watched this shit go back and forth, back and forth, over a generation now. First it was mainframes, everything centralized (“in the cloud!”). Then the backlash against that, to DEC/VAX and minicomputers and decentraliation. Then those got centralized. Then the PC revolution, decentralizing everything, a computer on every desktop! Then networkng, NetWare, and all the computers went “client-server”, which was the “cloud” of its day, centralzed servers. Then people got fed up with that centralization, and went to individual PCs again. Then the Internet came, and it was all network again, but it was decentalized, people ran their own mail servers, their own web servers, it was an explosion of revolutionary decentralization. THen that went away, it all went centralized, and the “cloud” thing is taking that to ridiculous extremes– nobody runs their own servers, everyone has their data synced on Google or Apple or whatever. And now it’s finally time for security concerns to make people realize that storing your shit on Google or Apple or Amazon is stupid. People will attempt to reclaim local control of their stuff.
Back and forth, a dialectic, a pendulum, endlessly swinging.
handsmile
It would appear that if Mr. Greenwald is taken out of the equation, a civil discussion of NSA surveillance can ensue here. Imagine that. (Parson Meacham would be so proud of us.)
(Also goes to confirm a minor point I made contra dpm in yesterday’s “Quelle Surprise” thread donnybrook: that the reporting of Barton Gellman is not afforded the “same reception” as that of a certain polemicist.)
Omnes Omnibus
@Mnemosyne: Actually, I have been told that putting every keyword you can thing of in a footnote in a white font ensures that you pop for the machine and that it doesn’t show up when it is printed for a real human. I haven’t tried it myself.
@handsmile: Fewer comments though.
different-church-lady
@Mnemosyne: Thankfully, I’m almost certain a human will read this one.
As as far as the people who came up with automated cover letter reading, my list reads (in decending order): Stalin, pond scum, Pol Pot, career HR People, Hitler.
different-church-lady
@handsmile:
Gosh, I just can’t imagine why that might be…
Marie Burns
You don’t have to worry about exhausting your WashPo views. Just open a private window (Firefox & Google Chrome both have ’em, not sure about other browsers), & read all the stories you like. If you get close to the limit (20 for the WashPo), close the window & open another private window & you’re good to go for another 20. Etc.
Marie Burns
Scamp Dog
@Howard Beale IV: I’ve got an Apple ][+ that’s safe from all internet attacks. Mostly because (even if I turned it on), I don’t have a landline to connect the 300 baud modem to. AND it’s maxed out with 64k of RAM, woo-hoo!
Now if I could only get the 5.25″ floppy drive working again…
fuckwit
@bemused senior: SSL is already broken for another reason: If you have control of a certificate that is in the browser’s list of acceptable certificates or authorities (ever taken a look? it’s a long fucking list!), then you can do a man-in-the-middle attack like the above. NSA almost 100% certainly has access to certificates to use for this. T-Mobile and other ISPs specifically ship their phones with their own bullshit certificates accepted so they’re not even trying to hide the fact they’re hacking your shit. THey use this “for caching”, they say. Fuck that. It’s spying no matter what they call it.
Secure Sockets Layer isn’t.
Betty Cracker
@different-church-lady: Understood, and your policy is undoubtedly a wise one. Given the disparate nature of the relevant experience, it might make sense, as you noted, to be more general in describing it, while also linking it back to the skill set in the target position. Something like, “My experience with XYZ makes me uniquely qualified to do ABC, so I am confident I will quickly become a valuable asset to Engulf & Devour as a Kitten Skull-Fucker.” Or something along those lines. Anyhoo, best of luck!
Betty Cracker
@Marie Burns: Well, that makes all kinds of sense. Thank you, Marie Burns.
handsmile
Well since peace, love, and understanding (or at least a distracted detente) has broken out here, for the six or seven BJers who are not watching the World Series, a TCM alert:
At 10:00pm (EST), one of Burt Lancaster’s finest performances as The Swimmer. Based upon a short story by John Cheever, an American master of that literary form.
different-church-lady
@Betty Cracker:
Thank you! That’s exactly the strategy I was fumbling towards. With that vote of confidence I can stop fretting about taking the wrong approach and just focus on the wordsmithing.
Howard Beale IV
@bemused senior: At this point I’d rather make the worst-case assumption that SSL was compromised.
Keith G
I have all but given up being too serious about policy discussions here at B-J as long as Obama remains president. There is just too much defensiveness and identity politics involved. I think that much healthier and robust discussions about security issues and the state of health care policy will be possible starting January 2017.
Omnes Omnibus
@Keith G: Very little defensiveness or identity politics on this thread.
different-church-lady
@Omnes Omnibus: Well, it’s early yet.
Keith G
@Omnes Omnibus: Every once in a while the clouds do part and a NSA discussion somehow avoids a Greenwald-Snowden pro/con deathmatch (and similar variations).
Every once in a while.
Omnes Omnibus
@different-church-lady: I hope that isn’t the case. I think that there are people who really are interested in discussing some of these issues and I think that BC specifically crafted this thread to cater to those people and discourage excessive Greenwaldism, Obotism, nothingburgering, and/or hair-on-fire-ism. Folks are making an effort. The thread may be shorter than some others, but people have talked about the actual issues and/ot technology.
different-church-lady
@Keith G: Of course, it does help quite a bit when there’s not a layer of Greenwald smeared all over it.
different-church-lady
@Omnes Omnibus:
Agreed, and I’m glad you name checked her for that.
bemused senior
@fuckwit: Not germane as to Google or Yahoo use of SSL. Their certs are not from dodgy CAs. So the dodgy CA threat is only relevant if you get tricked into going to a fake gmail or Yahoo mail site, which is pretty unlikely if you pay attention. The point is, the WaPo article explicitly states that the NSA cracked into the internal production network, behind the SSL gateways. They wouldn’t be the first to do this. Both these companies run >500,000 servers in their production nets, and trust me, it is not easy to see to it that they are all locked down at every level. There are also exposures at some of the data centers not owned by these companies, such as leased facilities overseas. It is a battle to keep the bad guys out, even if they don’t work for the feds.
bemused senior
@fuckwit: So, the attack with a dodgy cert could also work in combination with a poisoned DNS, so that resolution of gmail.com took you to the NSA, and the bad cert confirmed your mistaken view that you were at the real gmail site. This kind of attack couldn’t be carried out massively without being very noticeable, because the MITM would have to arrange to forward the captured mail to the real gmail site. Else it wouldn’t appear in the mail archive, etc., etc.
@Howard Beale IV: The problems with SSL are real, but when you look at the details of the possible attacks, ask yourself if it could be used for a massive ongoing data collection operation upon an infrastructure with a lot of saved state, such as one of the major web mail providers.
different-church-lady
Sox are three outs away from another WS championship, and some friends finished assembling my cover letter for me out of the collection of random parts I handed them.
It’s a great night.
Omnes Omnibus
@different-church-lady: If it’s a pieced together thing, make sure you reread it for continuity. I have fucked that up in the past.
different-church-lady
@Omnes Omnibus: I still need to apply some caulk and a layer of paint, so that’lll happen. But thanks for having my back.
Betty Cracker
@different-church-lady: Sometimes shit just works out, and thank bloody god when it does! Life is hard enough otherwise. Hope you get the gig. Go Sox!
Omnes Omnibus
@different-church-lady: No problem. I am a poor editor of my own writing, like many people, because I tend to “see” what should be there rather than what is there. I need multiple reads looking for different things each time. Editing and proofing usually takes me far longer than writing.
Howard Beale IV
@bemused senior: I have no doubt that that SSL attacks are not only real, but given the resources of the NSA it’s all but certain that SSL is borked.
different-church-lady
@Omnes Omnibus:
Me too. And it’s funny, but I’ve discovered musicians can be the same way about their music — when you play back their takes, they tend to hear the notes they intended to sing or play rather than the pitches they actually sang or played. I learned over time that I couldn’t count on a lot of them to be good judges of their own performances because were hearing the music metaphysically, with their brains instead of their ears. I have something close to perfect pitch, and so I stopped being passive in the control room and started pointing things out and they’d agree and say, “I didn’t hear that.”
Good editors and sounding boards are always valuable in creativity.
Elie
I’m late to the string again but wanted to thank Betty for again posting a great piece that is so so true — its maddening — all we have is the cartoon clouds and argle bargle..
beth
betty, your dumbest chicken has a good feel for information design. however, as a professional graphic designer who has made presentations (may powerpoint die a thousand painful deaths), i can assure you that an nsa graphic designer, however terrible they may be, was NOT in any way involved in making that slide. no professional designer would sanction the use of or use a smiley face.
that was totally the person putting together the presentation and i bet $100 internet bucks that the professional creatives in the communications department specifically told him or her (after he went ahead and gave the presentation without running it past the communication professionals) that that was a stupid and shitty, if trendily hand drawn, way to get the information across.
Jockey Full of Malbec
I’m flattered.
Joey Giraud
This thread is the real nothing burger.